Mimecast Launches Innovative Human Risk Management Platform
Organisations can now revolutionise their approach to mitigating employee risk with a new human risk dashboard and adaptive education solution.
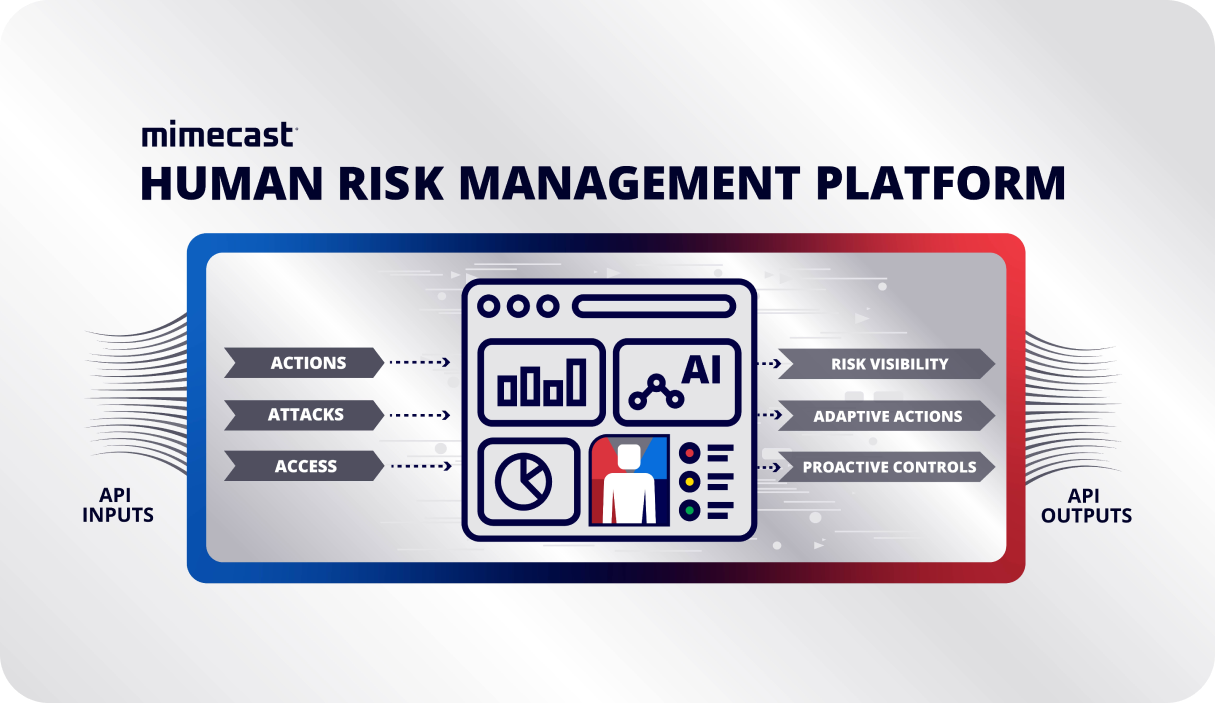
Mimecast, a global leader in cybersecurity, has unveiled its Human Risk Management (HRM) platform, marking a significant milestone in advancing towards the next generation of cybersecurity solutions. Responding to growing customer demand for more effective ways to reduce risk stemming from employee errors, Mimecast has introduced an integrated HRM platform. This platform offers unprecedented visibility into an organisation’s risk profile, scoring users based on risk and empowering security teams to educate and protect the most vulnerable parts of their workforce.
Human Risk Management Platform: Addressing Complex Challenges
A small fraction of users often account for the majority of security incidents. However, until now, organisations have relied on disparate security products that fail to differentiate between different levels of risk among employees. This results in frustrated users who disregard constant security warnings and bypass scattered controls, ultimately increasing both individual and organisational risk. Mimecast’s integrated HRM platform, built on a central risk engine, aims to counter evolving threats targeting human errors within organisations. The platform provides proactive controls and direct interventions to mitigate risks associated with behaviours such as clicking on malicious links, opening harmful attachments, or unintentionally sharing sensitive documents.
In today’s interconnected environment, employees have access to numerous collaboration tools and vast amounts of organisational data, making them prime targets for sophisticated attacks like business email compromise (BEC) and phishing. However, their constant multitasking and use of multiple tools also make them more susceptible to errors. Traditional security measures often fall short in addressing these human-centric risks, leaving organisations vulnerable.
“Our platform focuses on safeguarding organisations against employee errors and user mistakes, integrating essential defence and data controls to deliver one of the most comprehensive approaches to human risk management,” explained Marc van Zadelhoff, CEO of Mimecast. “We offer a unified solution that consolidates various technologies – from Mimecast and numerous partners – to help organisations protect collaboration environments and engage employees in risk mitigation.”
Human Risk Dashboard: Unmatched Visibility
The HRM platform features an innovative human risk dashboard, offering security teams company-wide risk scoring and visibility based on event data from native Mimecast metrics as well as current and future integrations with third-party tools. Beyond providing enhanced visibility at organisational, group, and individual levels, this dashboard quantifies attack factors by measuring the frequency and severity of inbound threats. Plans include analysing inbound phishing attempts, blocked malware, malicious web content from visited sites, and more. With complete access to this data, organisations can tailor security strategies accordingly, including awareness initiatives that provide targeted training where most needed and less where it’s not.
Mimecast Engage™: Revolutionising Security Awareness
A cornerstone of the platform is Mimecast’s new human risk awareness training, Mimecast Engage™, designed to redefine how security leaders manage human risk. Traditional security awareness programmes typically adopt a one-size-fits-all approach, making it difficult for IT leaders to identify high-risk employees or effectively mitigate risky behaviors. Mimecast Engage technology integrates insights from the human risk dashboard with the awareness training product acquired from Elevate Security in December 2023. This integration eliminates blind spots by offering extensive visibility into risky behaviours and tailoring interventions to each employee’s unique risk profile. This approach also boosts productivity by minimising interruptions for low-risk employees, allowing them to focus on critical business tasks.
“Mimecast Engage awareness and training empowers security teams to identify and mitigate risky behaviors with smarter, targeted training interventions,” said van Zadelhoff. “It leverages risk insights from the Mimecast ecosystem and beyond to deliver contextual interventions at the point of risk, enhancing overall workspace security.”
Key Benefits of the Human Risk Management Platform:
- Visibility: The comprehensive human risk dashboard covers the collaborative landscape, helping organisations stay ahead of evolving threats.
- Insight: With over two decades of cybersecurity expertise, Mimecast’s HRM platform aligns cyber and human risk for detailed, actionable insights, enabling informed decision-making by CISOs and security analysts.
- Action: The AI-powered platform ensures rapid threat detection and elimination, supporting precise, proactive decision-making.
Mimecast is driving innovation in human risk management. Its HRM platform and Mimecast Engage technology set a new standard for security, embedding protection into every facet of human interaction in an increasingly complex digital world.
Take Action on Human Risk Today
Don’t wait for a security incident to expose vulnerabilities in your human risk management strategy. Strengthen your defences now by implementing a comprehensive approach to managing employee risk. Our team offers tailored solutions, from advanced visibility into risky behaviours to automated security awareness training, helping you stay ahead of potential threats. Get in touch to find out how we can support your organisation’s cybersecurity efforts with proactive human risk management.