Welcome to our first CTO Insights newsletter. The aim is to provide you with some insights into what I’m seeing from our customers, vendors and the general IT trends in the key technology areas that are challenging us all as CTOs in our businesses.
In this first newsletter, I thought I’d go obvious with a couple of interesting articles and information across two of the hottest technology topics cybersecurity and generative AI (and I promise ChatGPT is not writing this newsletter).
Generative AI
The incredible popularity of ChatGPT (until the recent release of Threads, the quickest consumer technology to reach 100 million users, taking just two months, seven quicker than Tik Tok (Incredibly Threads did this in just six days!)) has taken the AI conversation from academic to one right into the heart of day-to-day use and of course day to day business.
I recently recorded a Tech Takeaways podcast with our COO, Jason Fitzgerald, on this very topic as we discussed the ins and outs of the technology. What it means and importantly what the risks and potential rewards are, feel free to watch or listen here.
What does all this mean for us as a CTO and our business?
When preparing for the podcast, I found a couple of useful resources that I wanted to share that provides a good overview into the rapidly evolving world of GenAI
Firstly, is this article for McKinsey What every CEO should know about generative AI | McKinsey. The article discusses what we mean by Gen AI specifically. Some of the use cases you will see across an organisation and some of the responsibilities, this is particularly useful for a CTO, we have before introducing such tech to our business.
For those who’d rather listen than read, I also find this podcast from an old friend of mine Yadin Porter de Leon who is at VMware, where he talks with Paul Roetzer, CEO of Marketing AI Institute, again, about the possibilities and potential risk. Including an interesting discussion on the impact on people. Find it here Generative AI: What CIOs Need to Know – with Paul Roetzer, CEO of Marketing AI Institute – CIO Exchange (vmware.com). They should provide you with a good overview of the space and what to consider.
Gen AI is not going to go away; this is going to become an integral part of day-to-day business and life. As CTOs, it’s important to develop a position on the topic for our organisations, that doesn’t necessarily mean being an expert, but it is important to understand how we can use this to drive our business better and what we should be wary of.
Cyber Security
Always at the top of the priority list is cybersecurity, it’s of course a problem that continues to evolve, with threats and attack approaches continually changing (see above!) Tackling cybersecurity requires us to continually evolve our understanding of the problem and our approach to tackling it.
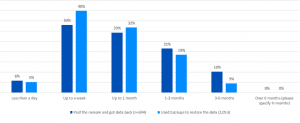
With that in mind, I recently presented alongside Sophos at an event in Liverpool where we were outlining the latest trends. I Was joined by Sophos Technologist Jon Hope who also shared the latest Sophos Ransomware report (you can get a copy of that here – 2023 Ransomware Report: Sophos State of Ransomware).
I also put together a blog post sharing some thoughts from the event you’ll find it here.
While we are talking about events. I also attended Infosec Europe in London at the end of June. These are always interesting events and chances to hear from subject experts and by chatting with vendors to gain an understanding of strategic direction and trends in the cybersecurity space.
It’s a big event and even across the two days I was there it was impossible to visit everyone, but I was lucky enough to get personal briefings from 8 different vendors as well. If you went to Infosec I’d like to hear your thoughts on what you saw, but if not – here’s a blog post I wrote with some of my key takeaways.
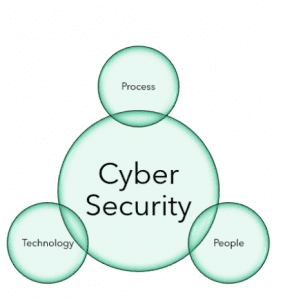
Cybersecurity is a multi-layered complex problem and needs us to consider security implications from core to edge. It’s about people, process and technology and balancing those three elements to ensure our security posture is strong and meets the needs of our organization. There’s no surprise that it’s likely to be a regular feature of future newsletters.
And Finally
Two bits of Microsoft news. Firstly, it recently made a number of announcements regarding its Entra platform. Entra is the name for Microsoft’s Identity security and access control tools. I’ll share more about this in the next newsletter, as there’s some interesting things in there. One thing I did want to share was the rebranding of Azure Active Directory to Entra ID. It does make sense in terms of the bigger picture of what they are doing, but thought It was worth giving a heads up, so if you see the name Entra ID and wonder what it is, then now you know. (BTW this does not impact Active Directory, just its Azure equivalent).
Secondly, is the impending end of support coming on Windows 2012 R2, October 10th is the end data and then it will no longer receive updates, including security, bug fixes or technical support. So, if you are still running Windows 2012R2 in your environment, now’s the time to change. More details here from Microsoft.
For now, thanks for taking the time to read this. If there is anything you’d like me to cover, you can drop me a note at cto@gardnersystems.co.uk find me on LinkedIn or Twitter and Threads @techstringy.
If you’d like to book in a call, you can also do this here


 Many of you would have met Paul during his time at Gardner’s. But for those that haven’t here’s a little about our new CTO. Paul studied Computing at Liverpool John Moore’s University. He got his first IT role at a pharmaceutical company in Liverpool, where he first met the Gardner Systems Team. He joined Gardner’s not long after and has worked across the business, from technical support to systems architect and today as CTO.
Many of you would have met Paul during his time at Gardner’s. But for those that haven’t here’s a little about our new CTO. Paul studied Computing at Liverpool John Moore’s University. He got his first IT role at a pharmaceutical company in Liverpool, where he first met the Gardner Systems Team. He joined Gardner’s not long after and has worked across the business, from technical support to systems architect and today as CTO.